Business E-Mail Compromise / CEO Fraud
Summary
- With BEC/CEO fraud, criminals send e-mails in the name of superiors and try to persuade those affected to take ill-considered actions such as buying gift cards.
- CEO fraud e-mails often urge people to hurry and have an atypical style of language for the supposed sender.
- Only the use of digital signatures offers real security regarding the true origin of e-mails.
- Report suspicious e-mails to TUD-CERT and warn your colleagues!
Introduction
Business Email Compromise (BEC) or CEO Fraud aims to deceive employees by misusing the identity of their superiors. This form of fraud poses a serious threat to universities and companies alike and can cause millions of dollars in damage.
Criminals take advantage of the fact that the sender name and sender email address in unsigned emails are generally not trustworthy and can be freely chosen on the sender side. This is comparable to letters or postcards, on which you can also write any sender address. In contrast to conventional phishing attempts, which usually involve links to untrustworthy websites or malicious attachments, criminals use CEO fraud to try to persuade their victims in a conversation to take ill-considered actions. Typically, this involves the purchase of gift cards worth several hundred or thousand Euros. However, there have also been known cases in which transfers in the millions have been initiated: The Pathé case, for example, was picked up by the media with $21 million in damages.
How to recognize fraud attempts
While in conventional phishing e-mails with malicious links or malicious attachments, the sender’s e-mail address and name have practically no relevance and can be freely chosen by the attackers, business email compromise, or specifically CEO fraud, is a special case, as a conversation requires to maintain a communication channel. Attackers usually achieve this by combining a real sender name (typically that of a superior) with an e-mail address that actually exists but does not belong to the alleged sender name (and is controlled by the criminals instead).
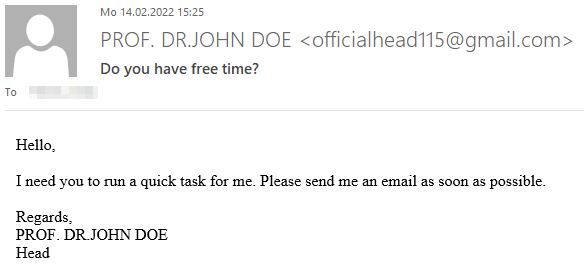
In the example below, the e-mail pretends to be from Prof. Dr. John Doe, but was sent from the email address officialhead115@gmail.com controlled by the attackers. Replies to this email are therefore sent directly to the criminals, but not to the actual e-mail address of Prof. Dr. John Doe.
Unfortunately, some e-mail programs only display the sender’s e-mail address after several clicks, which makes it difficult to quickly check for legitimacy. This is particularly a problem on smartphones, where the small displays reduce the immediately visible information to a bare minimum. For example, in the screenshot below, the sender’s e-mail address is missing:
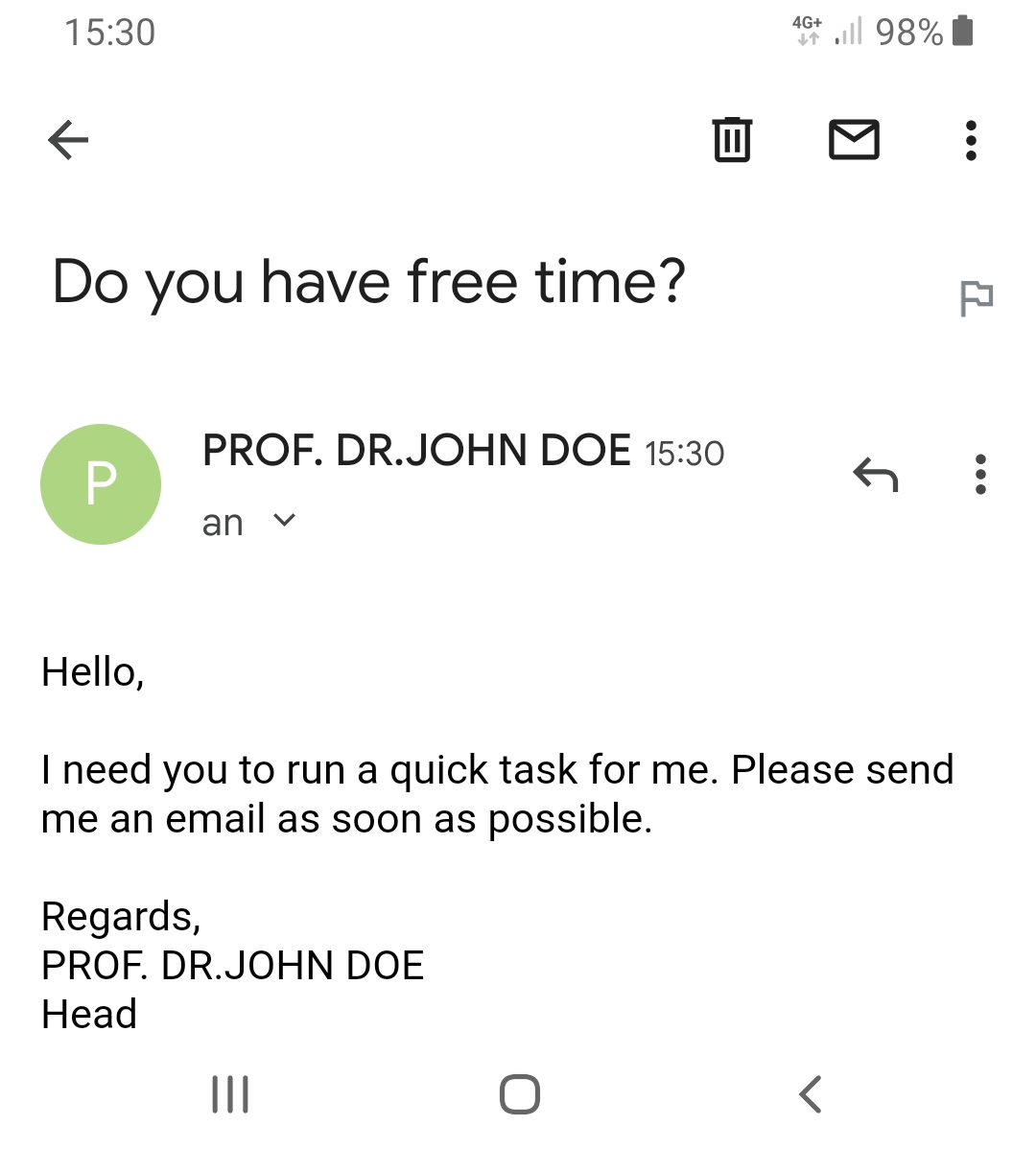
The procedure required to display the sender’s e-mail address depends on the app in use. Typically, a short or long tap on the sender’s name provides more information. Alternatively, check the e-mail on a PC before you think about replying. If you are unsure, ask your colleagues for advice or report the email to TUD-CERT.
Apart from the sender’s e-mail address, e-mails of this scam type convey a high level of urgency (“as soon as possible “), which is similar to conventional phishing attempts. In addition, their language style is often atypical for the perceived sender. However, you can only be absolutely certain of the authenticity of an e-mail if it has been digitally signed by the sender.
Dealing with fraud
The fact that Business E-mail Compromise is not just a theoretical problem becomes clear to us at TUD-CERT every day as we process incoming reports. In order to curb these fraud attempts, we block the sender e-mail addresses used by criminals as quickly as possible, but we are heavily dependent on your support. Unfortunately, fraud attempts are sometimes successful, which usually results in financial losses for those affected. We know from other universities that we are not the only ones to be confronted with such cases.
If you’re curious what dangers lurk in a reply to such malicious e-mails and how exactly the criminals proceed, we have prepared a graphic example of a case that occurred at TU Dresden in November 2023. The communication is anonymized and the victim’s messages have been rephrased, but the criminals’ incoming messages have not been changed.
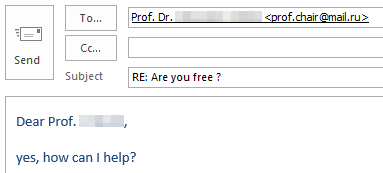
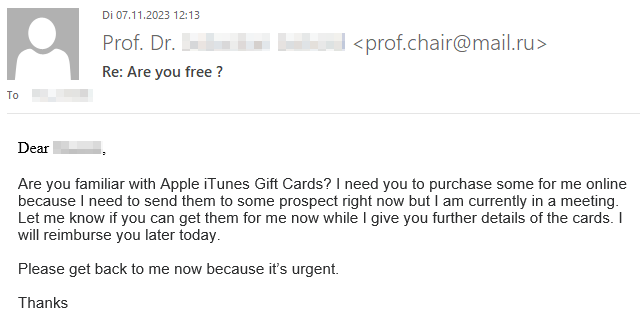
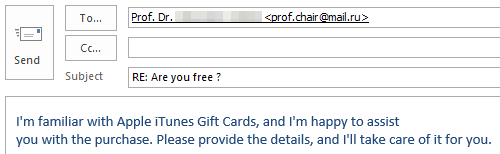
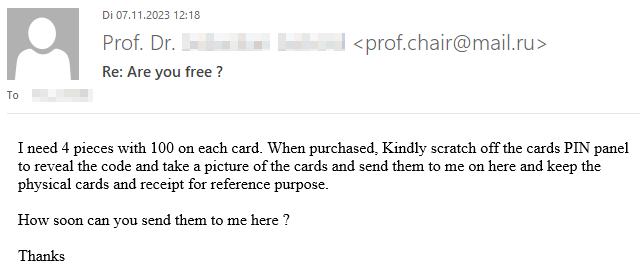
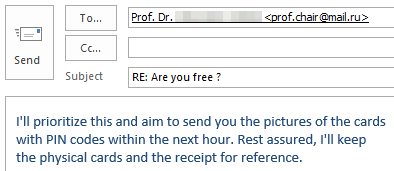
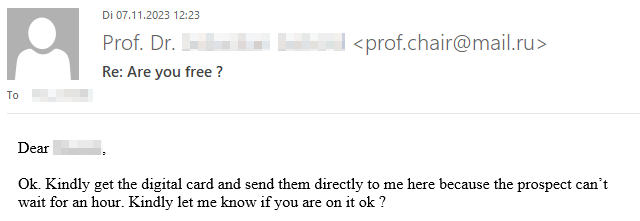
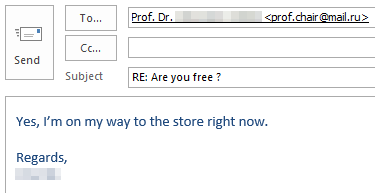
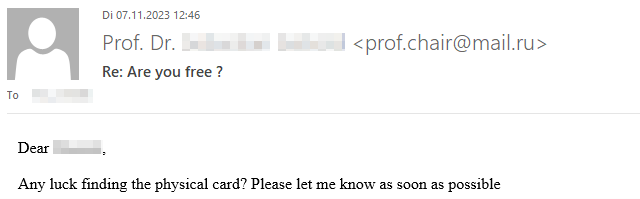
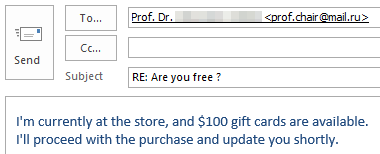
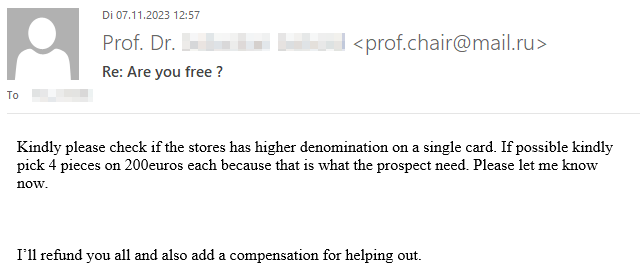
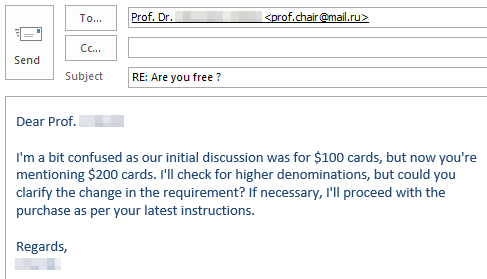
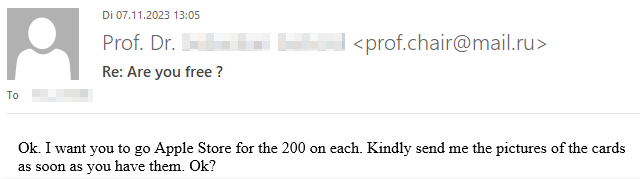
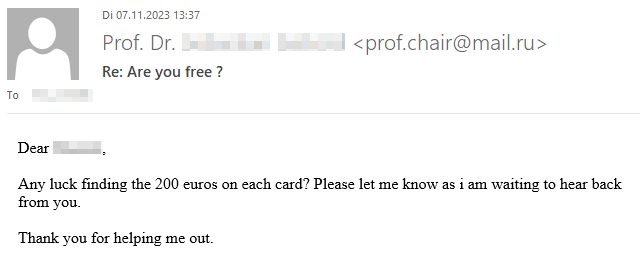
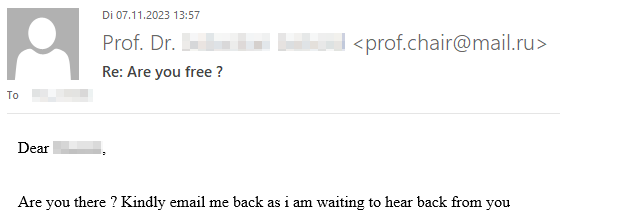
Fortunately, the criminals’ greed was their undoing and the victim broke off communication right in time due to growing skepticism.
Variations
This attack vector is not limited to e-mails. Criminals also actively abuse other digital communication services to impersonate supervisors or trusted individuals. In the conversation shown in the screenshot below, which is from November 2025, criminals use a WhatsApp business account to impersonate the rector of TU Dresden:
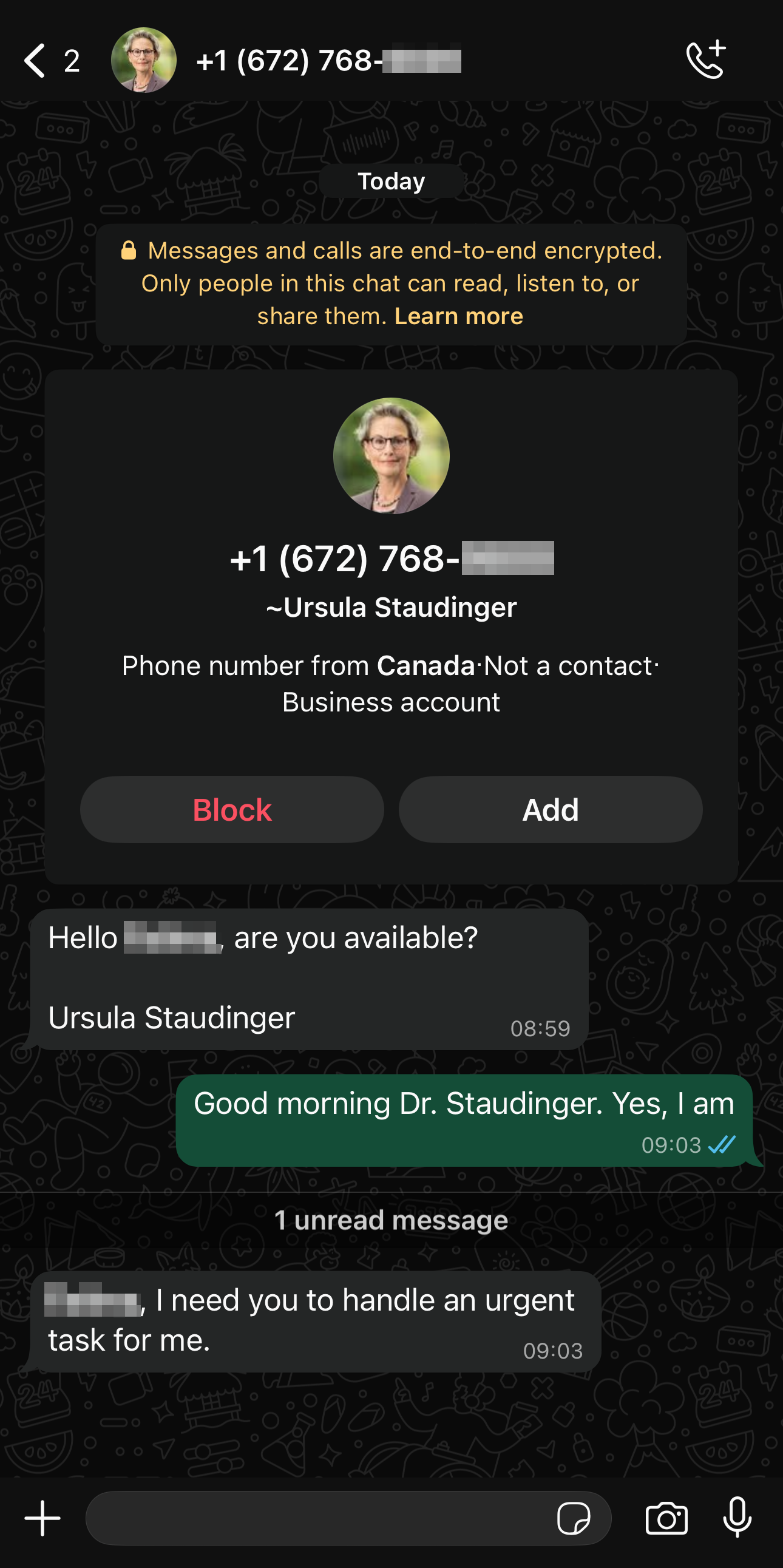
Please report these types of fraudulent activity both via the built-in reporting functions of the respective platform and to TUD-CERT via the e-mail address provided below.
Report
How to report phishing attacks to minimise the threat.
If an E-Mail that hasn’t already been automatically classified as spam/junk seems strange to you, please forward it to TUD-CERT. We evaluate them and initiate countermeasures if necessary. This way, we can reduce the risks of phishing e-mails, take phishing websites offline at an early stage and analyze malware distributed via E-Mail.
Currently we provide phishing reporting plugins for Microsoft Outlook and Mozilla Thunderbird, which can be used to submit questionable E-Mails to TUD-CERT with just a single click. For further details, please take a look at our installation and operating instructions. Alternatively, if you use E-Mail client software for which no reporting plugin is available, you can forward suspicious E-Mails directly to us via cert-meldung@mailbox.tu-dresden.de, ideally in raw format with complete header data. Please note that we will process all reports promptly, but will only get back to you if there are any follow-up questions.
Please note that the reporting e-mail address and plugins are only available for members of TU Dresden.
Microsoft Outlook
The phishing report plugin for Outlook adds a button to the ribbon bar to report the currently selected E-Mail directly to TUD-CERT.
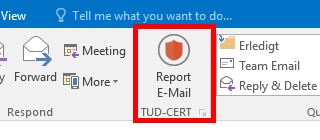
Below you can download the plugin directly, for details please consult our installation and operating instructions.
- Phishing Report Plugin for Microsoft Outlook v4.6.7.365: Installer for single users - ZIH login required
- Phishing Report Plugin for Microsoft Outlook v4.6.7.365: System-wide installer (all users) - ZIH login required
Mozilla Thunderbird ESR
Our phishing reporting plugin for Mozilla Thunderbird ESR (Extended Support Release) adds a report button to the message area, which can be used to report the currently displayed E-Mail directly to TUD-CERT.
The plugin can be installed directly from Thunderbird via the official Mozilla Add-On Website. For details please consult our installation and operating instructions. The Thunderbird plugin is available under an open source license, further development can be tracked in the associated repository on GitHub.